On October 16th, Cisco released a Security Advisory about two zero-day vulnerabilities affecting Cisco IOS XE Software with the web UI feature enabled in which attackers were able to gain administrator privileges and take over vulnerable routers. Because the web UI feature is enabled through the ip http server or ip http secure-server commands, the vulnerabilities affected systems for which the HTTP Server feature was enabled.
Network engineers everywhere dropped everything to check all their Cisco IOS XE devices across their network infrastructure and remediate potential instances where the vulnerabilities had been exploited. This is not the first time this has happened, and I suspect it won’t be the last. I don’t miss those periods of stress, late nights, and a lot of CLI entry that came along with news of security vulnerabilities.
Cisco later released software updates to address the issues. But it’s not like this recent set of vulnerabilities was the first — for any vendor or device type. As network engineers and operators, it’s crucial to be on top of security vulnerabilities and to remediate issues as quickly as possible. But how do you do that when your network infrastructure continues to expand across new domains, new regions, and an increasing number of devices and systems?
Automating Checks & Remediation with Itential
The Itential Automation Platform makes it easy to automate device scanning, report generation, and device remediation all in one workflow. Itential reduces the manual effort required to perform checks and remediations across devices.
Automating this process reduces the potential window in which your infrastructure is vulnerable to being exploited by attackers and helps you respond to security vulnerabilities without slowing down progress on your existing priorities.
I recently shared a demo focused on the recent Cisco IOS-XE vulnerability specifically. You can watch the demo here to see how I set up, build, and execute the workflow step by step.
Of course, these specific vulnerabilities have since been addressed and you have likely already run compliance checks and performed remediation activities across the Cisco IOS XE devices in your environment. But the process I followed in the demo to automate scans and remediation can apply to other vulnerabilities on other device types as well.
Here are the steps I took to check, report, and remediate the recent Cisco IOS XE vulnerabilities using Itential:
- Create a Device Group that includes all Cisco IOS XE devices in your infrastructure, federated across any number of connected networks, domains, and locations.
- Build a Golden Configuration policy to detect HTTP and HTTPS configurations on those devices and disallow them.
- Build an orchestrated workflow with different automated steps:
- Scanning devices in the Device Group.
- Execute the Golden Configuration rule.
- Generate an HTML report to be visualized in the platform and an email to be sent to required teams/individuals.
- Perform remediation activities for affected devices.
- Setting up a scheduled trigger so the workflow can run nightly without manual effort.
Device Group
Itential’s inventory federation is one of our platform’s unique capabilities that streamlines how you manage devices across a large, complex network. Itential federates your devices and allows users to perform actions for all devices of a given type across different networks, domains, and locations. You can learn how this patented approach to federation works in this white paper.
Once a device group is created, containing all potentially vulnerable devices across your infrastructure, you can refer to it in an automated workflow to run device scans and remediations.
Golden Configuration
A Golden Configuration policy is a rule or set of rules that can be applied to devices across your federated inventory. For the recent October vulnerabilities, a user would build a policy to check for HTTP and HTTPS configurations and disallow the commands ip http server and ip http secure-server.
Golden Configuration rules in Itential can also be built into ‘trees’ with hierarchical designations, so that some additional rules can apply to a subset of devices within a certain device group. Learn more about Golden Configuration templates in Itential here.
Process Orchestration Workflow
This is where the device group and Golden Configuration can both be utilized. Itential provides a low-code drag-and-drop canvas for building workflows that connect different automations together, allowing a single, end-to-end orchestration of the entire process: scanning devices, executing Golden Configuration, generating reports, and performing remediation. Learn how to build Itential workflows with these demos.
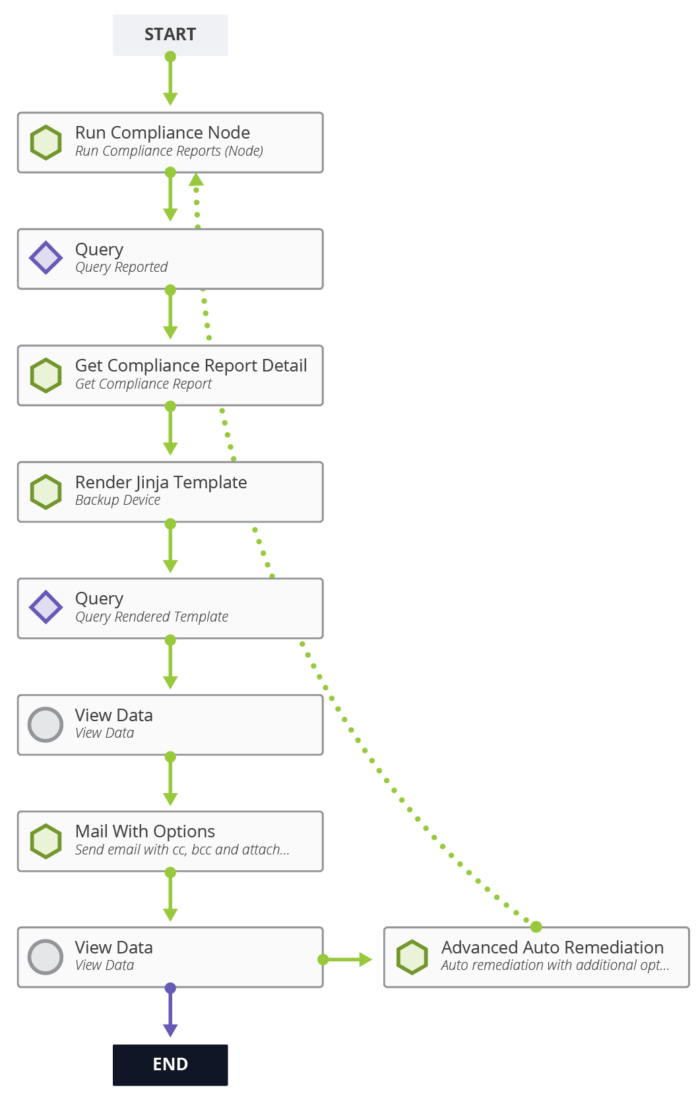
Here is what the Itential workflow from my Cisco IOS XE remediation demo looked like:
- First, the workflow automatically runs a compliance check to determine which devices have the HTTP or HTTPS Server feature enabled.
- Then, there are steps to get the details of the compliance report and generate a report using a Jinja template to display the result of the compliance check for each device where this workflow is run. This will be displayed in the platform and also sent as an email.
- Lastly, there is the ‘Advanced Auto Remediation’ step which contains the commands populated on the Golden Configuration rule. After remediation is performed, the workflow kicks back to the compliance check in order to validate that the device has been remediated correctly.
Scheduled Automation Trigger
Itential enables users to trigger automations in a variety of ways, including API calls in other systems like pipelines and event triggers based on changes on external systems. For security scans, though, you can take a simpler approach and use a scheduled trigger. This simply runs the workflow on a regular cadence as often as you’d like — especially useful for overnight scans.
Again, to dive into a more specific example of this approach to automated scanning, report generation, and remediation, check out this demo focused on the recent Cisco IOS XE vulnerabilities in October. Even if you’ve already solved for the issue from October, learning how to build device groups, Golden Configuration rules, and an orchestrated workflow can help Itential users address future vulnerabilities with confidence.
As network infrastructure continues to expand, managing security across your environment becomes more difficult. Itential gives you the tools to keep up, enabling easy automation of each step of the checking and remediation process, orchestrated as a single workflow that you can execute across every potentially affected device.