Share this

Table of Contents
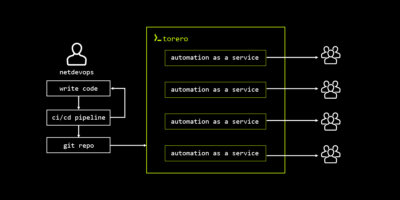
torero 1.6 is here, and this release is all about flexibility. Whether you’re managing shell scripts, custom binaries, or private Git repositories, torero 1.6 gives you the tools to integrate virtually any executable into your automation workflows.
Since 1.0, we’ve focused on making network automation accessible through Python, Ansible, and OpenTofu. With 1.6, we’re taking that even further by letting you run any executable file on your system – shell scripts, compiled binaries, you name it – all through torero’s unified execution architecture.
Let’s dive into what’s new.
>_ what’s new in torero 1.6
⚙️ Executable Objects
First up: Executable Objects. Think of these as reusable references to executables on your system. Instead of hardcoding paths to interpreters or binaries across multiple services, you create an executable object once and reference it wherever you need it.
This is particularly useful when you have:
- Multiple Python versions installed and need consistency across services.
- Custom-built executables that aren’t in your system PATH.
- Specific tool versions that need to be pinned across your automation.
Creating an executable object is dead simple:
>_ torero create executable-object bash --exec-command /bin/bash
Or for a specific Python version:
>_ torero create executable-object py312 --exec-command /usr/bin/python3.12 --description "Python 3.12 interpreter"
Once created, you can reference these objects when creating any service type – Python scripts, Ansible playbooks, OpenTofu plans, or the new executable services.
???? Executable Services
Here’s where things get interesting. Executable Services let you run any executable file through torero’s service management system. Shell scripts, compiled binaries, custom tools – if it can run on your system, torero can manage it.
The workflow is straightforward: create an executable object pointing to your interpreter or binary, then create a service that uses it.
>_ torero create executable-object bash --exec-command /bin/bash >_ torero create service executable backup-script \ --executable-object bash \ --repository scripts-repo \ --filename backup.sh
One of the powerful features here is argument formatting. You can customize exactly how arguments are passed to your executable:
>_ torero create service executable env-setup \
--executable-object bash \
--repository scripts-repo \
--filename setup.sh \
--arg-format "{{.Key}} {{.Value}}"
Now when you run the service with –set NAME=myapp –set PORT=8080, torero passes them exactly as your script expects. No more wrestling with argument formats.
And yes, secrets work here too. You can inject sensitive values as environment variables, keeping credentials out of your scripts and command history:
>_ torero run service executable api-caller \ --set endpoint=https://api.example.com/data \ --set-secret name=api-token,type=env,target=API_TOKEN
???? Repository HTTP Basic Auth
Private repositories just got easier to work with. torero 1.6 adds support for HTTP Basic Authentication, so you can pull from private repos using HTTPS URLs without needing SSH key infrastructure.
Store your token securely:
>_ torero create secret github-token --value <your-github-token>
Then associate it with your repository:
>_ torero create repository my-private-repo \ --url https://github.com/example/private-automations.git \ --username <your-username> \ --password-name github-token
This complements the existing SSH key support, giving you flexibility in how you authenticate with your Git providers. Use SSH when you have key infrastructure in place; use HTTP Basic Auth when tokens are more practical.
>_ additional improvements
Beyond the headline features, we’ve also addressed some important items:
Bug Fixes:
- The additionalProperties field in decorators is now properly respected when passing additional arguments with –set during service execution
Security:
- Updated the viper dependency to address potential vulnerabilities
>_ get started
Ready to try torero 1.6? Head over to torero.dev to download the latest release and check out the updated documentation.
???? download the latest version here →
???? check out the release notes here →
Have questions or feedback? We’d love to hear how you’re using torero in your automation workflows.
???? join us on the NAF Slack space in the #tools-torero channel
???? follow us on LinkedIn, X for the latest
⏯️ check out our YouTube channel for updates and tutorials
Stay tuned for more updates, we’re just getting started.