Executive Overview
The Department of Defense (DoD) relies on critical utilities – electricity, water, and telecommunications – to ensure operational readiness at bases worldwide. A cyberattack against these providers, especially as part of a broader adversarial campaign, could disrupt mission preparedness and readiness.
The increasing complexity of utility networks, and the growing number of interconnected network elements, make them more vulnerable to attack. A comprehensive, disciplined, and scalable approach to secure these networks is required.
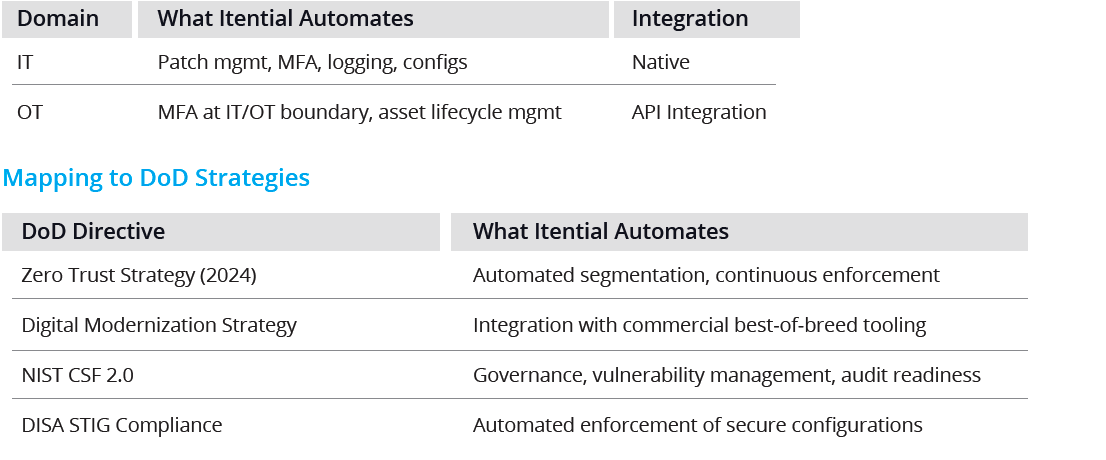
Network automation and orchestration is emerging as the operational backbone for securing and optimizing these networks. This paper explores the necessity of automation/orchestration for utilities serving DoD bases and demonstrates how Itential’s platform delivers these capabilities in alignment with the DoD’s Zero Trust Strategy, Digital Modernization Strategy, and NIST CSF 2.0.

Advanced Persistent Threats Targeting DoD-Aligned Utilities
Utilities supporting DoD bases are critical national security assets. The Volt Typhoon and Salt Typhoon campaigns highlight how state-sponsored actors are compromising telecom, water, and electric utilities to gain persistence in networks connected to DoD facilities.
Volt Typhoon Attack Chain
Volt Typhoon’s attack campaigns are characterized by:
- Reconnaissance to map network architecture and operational protocols.
- Initial access by exploiting unpatched or zero-day vulnerabilities in internet-facing devices (routers, VPNs, firewalls).
- Credential theft by escalating privileges and harvesting admin-level accounts.
- Domain compromise through Active Directory database extraction and offline hash cracking.
- Living Off the Land (LOTL) techniques to maintain persistence while avoiding detection.
- Movement toward OT environments to disrupt operational technology.
Salt Typhoon Persistence
Salt Typhoon, while similar in initial access methodology, has demonstrated extended persistence:
- Maintaining low-noise, long-term access to critical utility networks.
- Exploiting EOL devices and default configurations.
- Using dormant access to re-enter networks even after remediation efforts.

Joint Cybersecurity Advisory
The Government’s Call to Action
On February 7, 2024, CISA, NSA, and FBI issued a Joint Cybersecurity Advisory directing immediate mitigations.
Apply patches for internet-facing systems. Prioritize patching critical vulnerabilities in appliances frequently exploited by Volt Typhoon.
Implement phishing-resistant MFA across all privileged accounts.
Ensure logging for application, access, and security events is enabled and stored in a central system.
Plan for End-of-Life (EOL) technology replacement or mitigation to avoid unpatched exposure.

From Advisory to Execution: Why Automation Is Now Critical
The challenge is clear: these mitigations are operationally intensive, complex, and slow to execute manually – especially across diverse, multi-vendor utility networks.
Network automation uses software to perform repetitive operational tasks like patching, configuration, and monitoring – with minimal human intervention. Orchestration coordinates these actions across IT and OT domains, ensuring policies are enforced consistently at scale.
Key capabilities for utilities serving DoD:
- Automated patch deployment to close vulnerability windows quickly.
- Policy-driven configuration management to eliminate insecure defaults.
- Orchestrated incident response to isolate threats rapidly.
- Integrated IT + OT visibility to track assets, configurations, and lifecycle status.
This approach aligns directly to DoD Zero Trust priorities (segmentation, continuous verification, resilience) and creates a repeatable, scalable framework for defense.

Enforcing Policy at Scale: How Itential Protects DoD Infrastructure
Itential’s network automation and orchestration platform is designed to operationalize these concepts at the scale utilities require.
01 Automated Patch Management
![]()
- Integrates with vulnerability scanners (Tenable, Rapid7) to identify at-risk devices.
- Automates testing, scheduling, and deployment of patches across heterogeneous environments.
- Minimizes downtime with orchestrated maintenance windows.
02 Policy-Driven Configuration Compliance
![]()
- Enforces golden configurations aligned to DoD STIGs and NIST CSF controls.
- Continuously validates device configurations and remediates drift.
03 MFA Enforcement
![]()
- Automates phishing-resistant MFA configuration across VPNs, firewalls, routers, and IT/OT boundaries.
- Integrates with identity providers (Microsoft Entra ID, Okta, Cisco ISE).
- Continuously audit for MFA gaps and remediates misconfigurations.
04 Centralized Logging & Audit
![]()
- Automates logging enablement across all devices.
- Routes logs to SIEM systems (Splunk, Sentinel) and monitors for tampering.
- Maintains full audit trails for compliance and readiness.
05 End-of-Life Lifecycle Management
![]()
- Maintains a real-time asset inventory to identify EOL devices.
- Flags devices for replacement and applies compensating security controls until upgrade.
- Orchestrates replacement or mitigation workflows.

IT + OT Integration
Itential specializes in automating and orchestrating IT infrastructure, but integrates seamlessly with OT security tools like Tenable OT Security or Nozomi Networks to deliver a unified security posture.

Proven at Scale: Customer Results
The challenges utilities face in securing DoD-aligned infrastructure aren’t unique, they echo the same operational complexity, tool fragmentation, and compliance pressure seen in large-scale enterprise environments. Itential has already helped organizations in equally demanding sectors operationalize Zero Trust principles and security frameworks at scale.
Challenge
1,600+ annual requests for network and security changes, missed SLAs due to manual approvals and disconnected tools, and audit risk from inconsistent configuration/change documentation.
Solution
Itential orchestration across Cisco ISE, InfoBlox, Active Directory, and ServiceNow.
Results
- 1,670+ requests automated annually, eliminating repetitive manual work
- 834+ hours saved each year, reallocated to higher-value security tasks
- SLA compliance improved from delayed to near real-time
- Audit readiness maintained continuously with automated documentation
What this enterprise achieved at global scale is directly applicable to utilities serving DoD bases where patch cycles, access controls, and audit trails must be fast, accurate, and compliant.

The Mission Can’t Wait
The urgency to act has never been greater. Volt Typhoon and Salt Typhoon have demonstrated that adversaries are not probing for weaknesses, they are actively exploiting them. At the same time, regulatory and operational pressures are converging, leaving utilities with little margin for delay.
Active Campaigns in Progress
Volt Typhoon and Salt Typhoon are not theoretical; CISA and NSA confirm persistent access in multiple utilities that serve DoD facilities.
Operational Strain
Manual patch cycles, decentralized logging, and reactive configurations cannot keep pace with today’s threat tempo.
Regulatory Deadlines
DoD Zero Trust and CISA OT security guidance are moving from recommendations to expectations. Utilities must demonstrate tangible progress in segmentation, patching, and lifecycle management.
Procurement & Policy Alignment
FedRAMP-authorized cloud platforms and trusted integrators make adoption faster. Itential is available via these channels, enabling rapid alignment to DoD frameworks.

90-Day Plan to Secure Utilities Supporting DoD Bases
Day 0–14
Establish Control & Scope: Deploy Itential Platform with integrations to core systems – ServiceNow, Active Directory, InfoBlox, Cisco ISE; connect vulnerability scanners; baseline inventory and logs; define success criteria.
Output: Asset map, top 10 critical CVEs by device family, initial golden-config gap list, KPIs locked.
Day 15–30
Prove Patch Velocity: Pilot automated patching on two priority device families with maintenance windows and pre/post checks; target critical MTTR under 7 days.
Output: Executable runbook and scheduler, weekly MTTR trend, tested rollback.
Day 31–60
Close config & MFA Gaps: Enforce golden configurations aligned to STIG and NIST CSF; remediate drift; expand phishing-resistant MFA across VPNs, firewalls, routers, IT/OT boundary.
Output: 100% admin-MFA coverage, drift SLA ≤ 24 hours, nightly compliance report.
Day 61–90
Harden Visibility & Lifecycle: Centralize logging to SIEM, alert on tampering; establish EOL lifecycle workflows with compensating controls until replacement.
Output: 100% device log coverage, EOL inventory ≥ 95% complete, replacement queue live.
How You Will Measure Success:
- KPIs to report weekly: Critical patch MTTR, admin-MFA coverage %, device log coverage %, drift detected and resolved within 24 hours, EOL coverage %, automation wins (requests automated, hours saved).
- How to buy, fast: Leverage existing DISA pathways and proven ATO lineage to reduce risk and accelerate start. Common paths observed: GSM-O II with the prime, prototype OTAs for rapid pilots, or standard GWACs as needed.
- Decision this week: Select two device families and three representative sites for the pilot, schedule a 90-minute scope workshop, approve read-only integrations to begin Day 0 data collection.

Securing the Utilities That Power the Mission
Volt Typhoon and Salt Typhoon proved what’s at stake: the adversary is already inside the gates. For utilities that serve DoD bases, every unpatched device, every misconfiguration, every delayed control change is an opportunity for exploitation.
Itential is the execution layer for Zero Trust, Digital Modernization, and CISA-aligned security at scale. By automating patch cycles, enforcing configurations, managing lifecycles, and orchestrating rapid response, Itential transforms policy into practice across thousands of devices and complex environments.
The DoD mission relies on uninterrupted power, water, and communications. Securing these utilities isn’t just an IT priority, it’s a national security imperative. Itential enables utilities to deliver operational resilience, cyber defense, and mission assurance – every day, at every base.