Share this
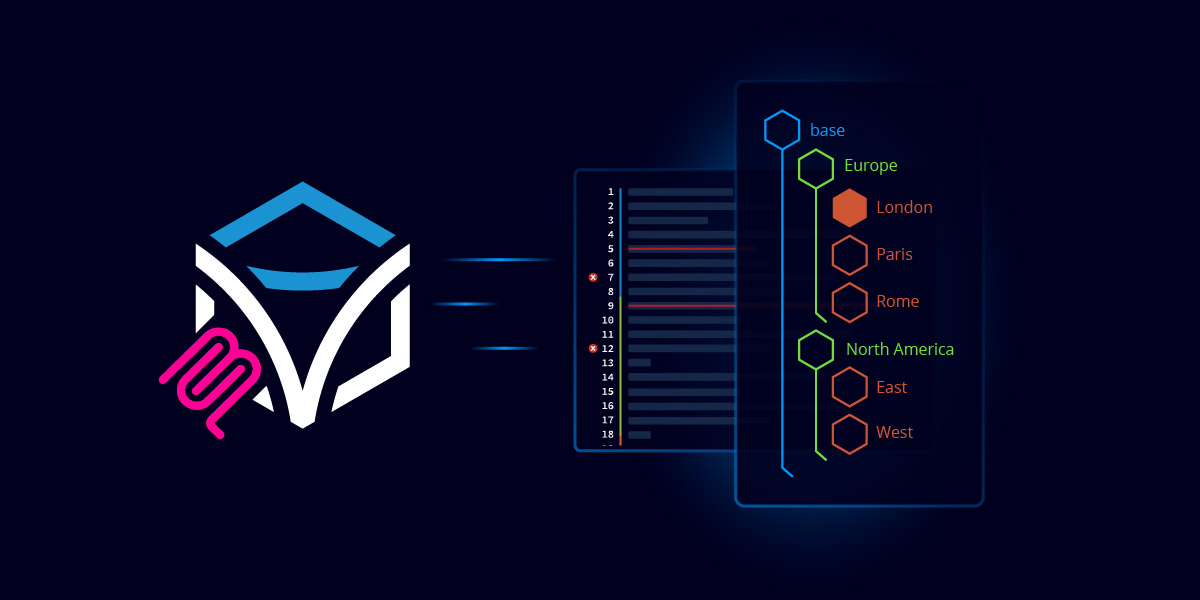
Table of Contents
Maintaining infrastructure compliance shouldn’t feel like cramming for an exam, yet most enterprises still stumble through audit season armed with outdated spreadsheets, tribal knowledge, and last-minute heroics. Regulatory frameworks such as NIST CSF, PCI DSS, ISO 27001, HIPAA, and SOX demand provable, continuous control across every device and environment. But manual reviews and fragmented documentation make that nearly impossible. The result is a vicious cycle of wasted hours, inconsistent configurations, and elevated risk from drift and blind spots.
There’s a better way. By pairing AI with the Itential Platform through our Model Context Protocol (MCP) Server, we’ve turned “Golden Configuration” from a static policy document into a living, version-controlled system of record that’s capable of validating every change in real time, across any vendor, at any scale.
Why Compliance Still Feels Like a Fire Drill
Most organizations do define a golden baseline, but it too often lives in a PDF or someone’s private Git repo. Enforcement is reactive: run a script after hours, generate a giant diff, and open tickets that linger for weeks. Drift accumulates because changes slip through during incidents, maintenance windows, or “just-this-once” exceptions.
The result is the same every quarter: wasted hours, audit anxiety, and the nagging sense that something is still hiding in the weeds.
Turning Documents to Validated Policies in Minutes
So, how do you go from a 400-page security policy document, written by lawyers and auditors to a set of clear and concise Golden Configuration templates that are specific to your network devices and environment? Today, it can take teams weeks or months to take that first step, even BEFORE they run the first audit.
That’s where Itential’s MCP server comes in. It integrates with the Itential Platform and your AI LLM of choice (ChatGPT, Claude, Custom LLM, you name it) to autogenerate all of those templates based on the current Policy Documents, and creates Golden Configuration trees that are categorized according to policy sections and specific to your network vendors. Here’s how it works:
Step 1: Prompt the AI
Prompt your AI to research the most current security policy documentation with a focus on generating a template that adheres to this standard specific to vendor CLI you are targeting. Then comes the Itential MCP magic – have it build and install those templates directly as Golden Configuration trees in the Itential Platform.
Step 2 Review and Modify the Golden Configurations
Review the newly created Golden Configuration trees in the Itential Platform, and modify the smaller details to better fit your network environment and the device configurations you are targeting. All the heavy lifting was done, so this is a breeze.
Step 3: Assign Devices and Execute Compliance Audits
Assign specific network devices/groups to the Golden Configuration tree and run your first audit, initially as a test making final changes as needed.
With that in place, you can get started running audits, generating reports, remediating devices, validating changes and ultimately ensuring that audits are no longer a source of anxiety. See how it’s done in this demo.????
Turning Policy Into Practice
In practice that means:
????️ Dynamic Compliance Management
Every proposed change is checked in real-time for compliance; no more surprises weeks or months later.
???? Vendor-Agnostic Adaptability
Cisco, Juniper, Arista, Palo Alto: Itential speaks to them all, so your policy is enforced consistently across multi-domain networks.
???? Actionable Insights
Reports expose trends, risk hotspots, and drift history, giving security and operations teams shared, trustworthy data.
How That Plays Out for Customers
One payments company that wrestled with forty-plus PCI controls used to dedicate an entire sprint to audit prep. After rolling out Golden Configuration Trees, the security lead runs a dashboard filter, exports a report, and shares it with the assessor all before lunch. Their network engineers now spend that freed-up sprint deploying automation for branch rollouts instead of combing through diff logs.
A healthcare provider saw something similar: drift-related incidents dropped, and mean time to remediation for config defects fell from days to minutes once MCP started rejecting non-compliant commits at the gate.
The Payoff in Plain Numbers
Customers typically report:
???? 80-90% reduction in audit preparation time.
⚡️Fewer service outages tied to misconfiguration or drift.
???? Happier engineers who focus on innovation, not fire drills.
???? Lower risk of regulatory fines thanks to continuous proof of control.
Those metrics echo across industries, from finance and healthcare to service provider networks, because the underlying pain is universal.
Where to Go from Here
If your team is still juggling PDFs, spreadsheets, and late-night diff scripts, let’s talk. I can show you a live demo of Golden Configuration Trees – complete with automated auditing, real-time validation, and auto-remediation on the device types you actually run. Start in a lab, prove it works, then scale at your own pace.
With AI-powered Golden Configuration Trees and Itential MCP, continuous compliance stops being an aspiration and becomes the invisible safety net your network deserves.