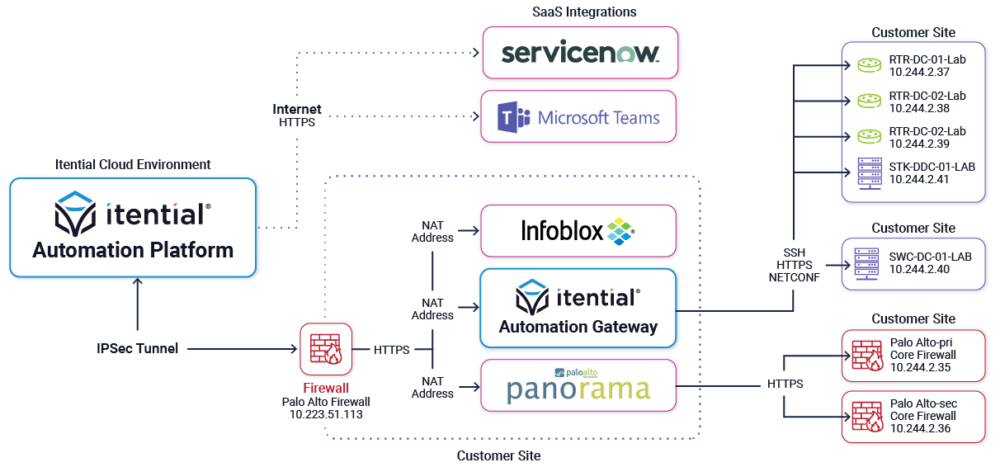
Itential Cloud (SaaS) Deployment Architecture
Overview
- Customer deploys a Gateway device to initiate an IPSEC VPN tunnel to the Itential VPN Gateway to connect to the Itential Cloud IAP
- This Customer VPN GW will be provided and deployed by the customer and must be compatible with Itential IPSEC capabilities.
- This solution provides an IPSEC VPN tunnel connection between Cloud-IAP and On-Prem Customer Gateway, and that tunnel is used for routed IP connectivity to the IAG and IT Systems at the customer’s premises.
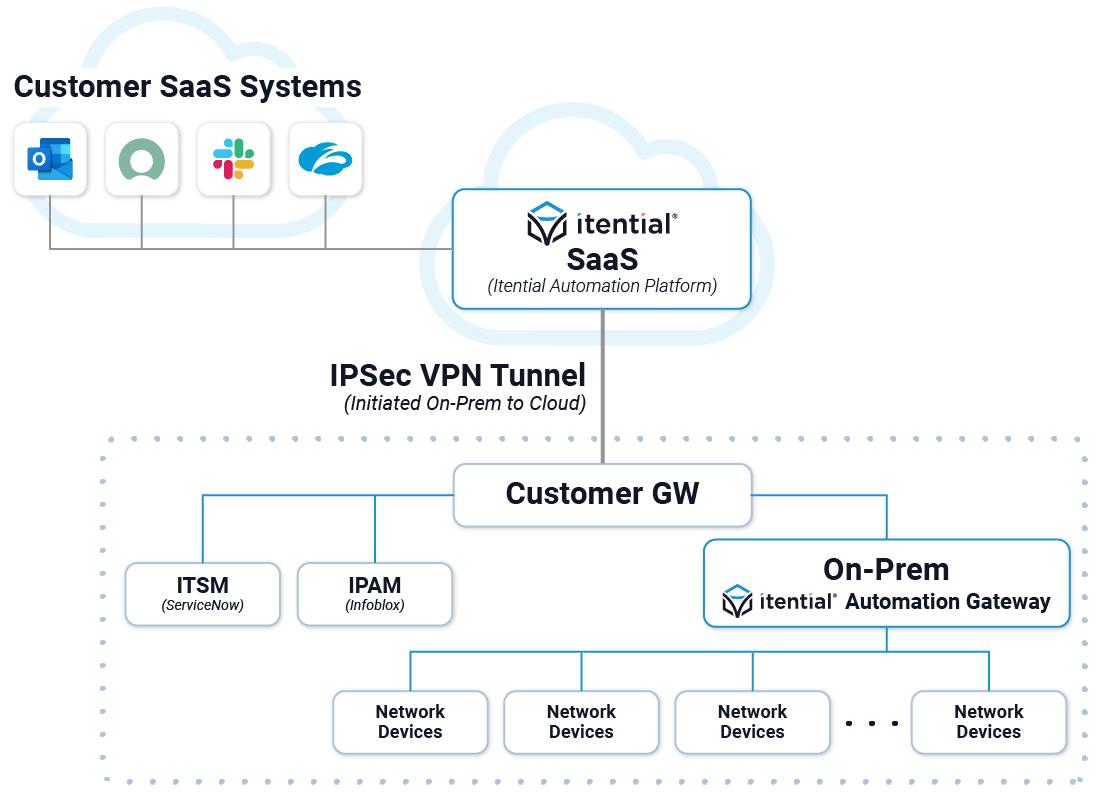
Security Within Itential Cloud (SaaS)
- SOC2 Type 2 Compliant (SOC2 Report can be made available on request).
- Onboarded administrator users for each Itential Cloud Customer will have access to Cloud Console where they can View and Manage Itential Automation Platform (IAP) Instances that belong specifically to their organization only.
- Each Itential Cloud Customer will have a distinct associated database which can only be accessed through Itential Automation Platform (IAP) based on their defined and assigned role within Itential Cloud Console.
- Customer Data is secure and encrypted both in transit and at rest.
- All sensitive data pertaining to platform configuration (application, adapter properties) can be encrypted during setup.
- Embedded RBAC within Itential Cloud Console enables Customer Admin to determine who would have access to any/all Customer IAP Instances (Development / Staging / Production).
- Embedded RBAC within Itential Automation Platform (IAP) enables Customer Admin to determine what activities users can perform within the automation platform based on their Roles.
Secure Connectivity Between Itential Cloud & Customer’s On-Prem Environment
- Site-to-Site IPSec VPN Tunnel between Itential Cloud and the Customers Gateway is established to provide secure connectivity for communication to all customer end systems.
- Itential Cloud & IAP uses SSL / TLS 1.2.
Control & Security Options for Customers
- Customers have Administrative privileges to add and remove users from Itential Cloud Console.
- Customers have Administrative privileges within Itential Cloud Console to limit / grant access to IAP Instances to relevant Customer personnel.
- Customers have the ability to control IPSec Connectivity into Customer’s Environment .
- Customers have the ability to control IP routing through their Customer VPN GW to limit/grant access to Itential Cloud for communication with any Customer managed end systems.
- Customers have ability to define security permissions within Itential Automation Gateway (IAG) to determine how IAG will communicate with Network Devices
- Customers may use firewalls or alternative methods to limit or block Itential Automation Gateway (IAG) from communicating with customer systems.
Itential Cloud (SaaS) Security Standards & Posture
Alignment with Compliance Frameworks
![]()
- SOC2 Type 2
Vulnerability Management Policy
![]()
- Daily Code Repository and Software image scans to assess vulnerability
- Vulnerability scans performed each major/minor Code Release on a Monthly Basis that Includes APIs, Dynamic Pages, and Core Functionality
- Itential uses criteria including standard scoring, trending vulnerabilities, reachability, availability of exploits, and other factors as inputs to its remediation process.
Risk Assessment Program
![]()
- Analyzed Annually
- Considers Critical Systems
- Factors Include:
- Risk
- Threat
- Likelihood
- Consequence
Incident Management Plan
![]()
- Includes Process for:
- Prevention
- Detection/Analysis
- Containment
- Eradication
- Recovery
- Notification to Impacted Parties
- Incident Documentation and Post-Mortem
- Annual Testing & Remediation
Platform Authentication & Authorization
![]()
- Integration with SAML Based Identity Broker
- Support for OpenId and Local User/Password
- Role Based Access Control (RBAC)
- Group Based Access Control (GBAC)
- Roles
- Product Developed
- Custom Roles
- Users & Groups (Managed in external AAA)
- MAP IAP roles to AAA Groups
Platform Auditing
![]()
- Audit Trail – Transactional Audits per Session Request
- Each transaction is identified with an audit ID
- Spawned child transactions are captured as part of the stack
- Stored in MongoDB audit_trail collection
- Track User Activity
- Automation Job
- Each task contains metrics
- Incoming / Outgoing payload
- Execution Path
- Stored in MongoDB jobs and tasks collections
Itential Cloud (SaaS): Example Deployment